Application Security (VAPT)
Vulnerability Assessment | Penetration Testing
Get a Quote – Secure Your Business Today!
OUR VAPT Sevices
Explore more resources with iSpyCyber for cutting-edge cybersecurity blogs, insights, tools, and others to stay ahead of threats.
Web Application
VAPT
Secure your websites with
comprehensive vulnerability testing to
identify risks, prevent data breaches, and
ensure robust application protection.
Mobile Application
VAPT
Protect Android and iOS apps against
evolving cyber threats by identifying
vulnerabilities, securing user data, and
maintaining compliance standards.
Network / Infra. VAPT
Strengthen internal and external
networks by identifying vulnerabilities in
servers, routers, and firewalls through
advanced penetration testing.
Thick client
Application VAPT
Assess desktop applications for
vulnerabilities in authentication, logic,
and data handling to strengthen security
and prevent exploitation.
API VAPT
Safeguard APIs from unauthorized
access and data breaches through
advanced testing that ensures integrity,
authentication, and endpoint protection.
SAP Application
VAPT
Protect critical SAP systems from
misconfigurations, privilege escalation,
and data breaches through deep security
assessments and remediation.
Blockchain
Application VAPT
Enhance blockchain resilience by
auditing smart contracts, consensus
mechanisms, and cryptography to
eliminate potential financial or
operational risks.
IoT VAPT
(Internet of Things)
Defend connected devices by testing
firmware, communication protocols, and
configurations to ensure secure IoT
environments and data protection.
OT VAPT
(Operational Tech.)
Safeguard industrial control systems by
identifying vulnerabilities in SCADA, PLC,
and ICS environments to prevent
operational disruptions.
Application Security Testing Methodology
Our testing methods include black box, gray box, and white box security testing, ensuring thorough vulnerability assessments from multiple perspectives for comprehensive protection.

Black Box
Black box security testing is a technique used to evaluate the security of a system or application from an outsider's perspective, without any prior knowledge of the system's internal workings. The objective of black box security testing is to identify vulnerabilities or weaknesses that an attacker might exploit to compromise the security of the system.

White Box
White box security testing, also known as clear box testing or transparent box testing, is a technique used to evaluate the security of a system or application by analyzing its internal workings, such as the source code, design, and architecture. In other words, the tester has full knowledge of the system's internal workings and can analyze it from a developer's perspective.

Gray Box
Gray box security testing is a technique used to evaluate the security of a system or application by combining elements of both white box and black box testing. In gray box testing, the tester has partial knowledge of the system's internal workings, such as access to limited design or implementation details.
VAPT Approach
iSpyCyber's VAPT process integrates agile methodologies and best practices: planning, reconnaissance, scanning, exploitation, reporting, remediation, and re-testing for comprehensive and adaptive security assessments.
Define Scope
Pre-Engagement
Reconnaissance on target
Define Scope
Pre-Engagement
Reconnaissance on target
Define Scope
Pre-Engagement
Reconnaissance on target
Define Scope
Pre-Engagement
Reconnaissance on target
Define Scope
Pre-Engagement
Reconnaissance on target
Define Scope
Pre-Engagement
Reconnaissance on target
Key Benefits
It’s an important practice that gives organizations visibility into real-world threats to your security. As part of a routine security check, penetration tests allow you to find the gaps in your security before a hacker does by exploiting vulnerabilities and providing steps for remediation.
Download VAPT Resources
It’s an important practice that gives organizations visibility into real-world threats to your security. As part of a routine security check, penetration tests allow you to find the gaps in your security before a hacker does by exploiting vulnerabilities and providing steps for remediation.
Compliance Commitment as Per Your Requirement











Discover more Resources
Explore more resources with iSpyCyber for cutting-edge cybersecurity blogs, insights, tools, and others to stay ahead of threats.
FAQ
Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive security process that identifies, analyzes, and mitigates vulnerabilities within your IT systems, networks, and applications. It helps organizations like yours prevent data breaches, protect critical assets, and comply with cybersecurity standards. At iSpyCyber, our expert team ensures your digital environment remains secure and resilient against evolving cyber threats.
iSpyCyber follows a systematic and industry-recognized VAPT methodology that includes information gathering, vulnerability scanning, manual verification, exploitation testing, risk evaluation, and reporting with remediation guidance. We combine automated tools and manual testing to uncover real-world vulnerabilities and simulate hacker-like attacks — ensuring your organization is truly protected.
Every system connected to the internet or internal network should undergo VAPT. This includes web applications, mobile apps, APIs, cloud infrastructure, IoT devices, network systems, and critical databases. iSpyCyber customizes VAPT services to fit your business environment — whether you’re a startup, enterprise, or government organization — ensuring full security coverage.
It’s recommended to perform VAPT at least once a year, or whenever there are significant changes such as new deployments, software updates, or infrastructure modifications. Regular VAPT testing by iSpyCyber ensures that newly introduced vulnerabilities are quickly identified and mitigated, maintaining ongoing compliance and security readiness.
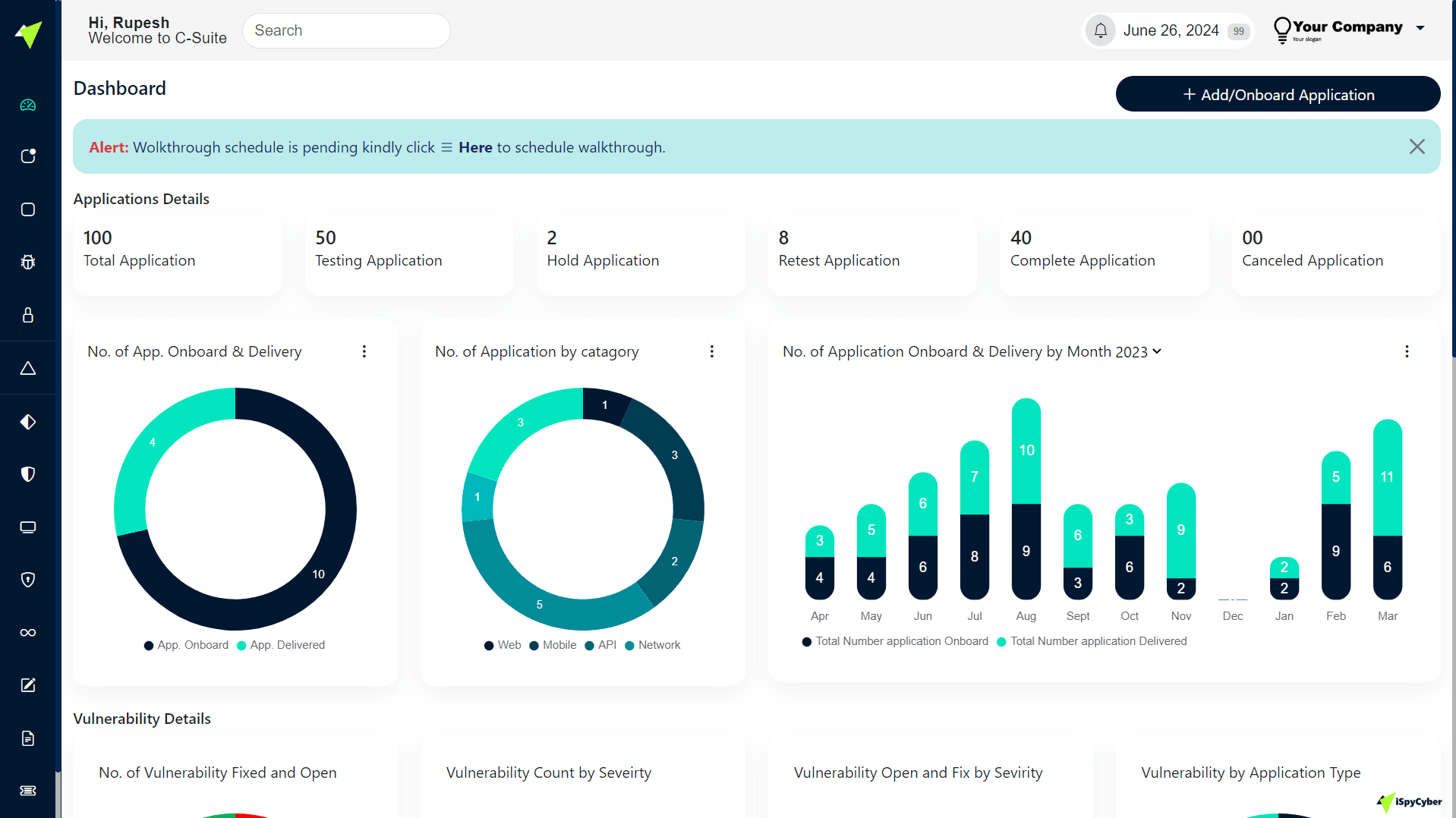
After the assessment, iSpyCyber provides a detailed VAPT report that includes:
Executive summary for management review
Comprehensive list of identified vulnerabilities
Risk rating (Critical, High, Medium, Low)
Technical details with screenshots and evidence
Remediation recommendations for each finding
These insights help your security and development teams take immediate, effective action to strengthen defenses.
At iSpyCyber, we strictly adhere to data confidentiality and ethical testing standards. All assessments are conducted under mutual NDAs (Non-Disclosure Agreements) and authorized testing scopes. We never disrupt business operations or access client data without consent — ensuring a safe, controlled, and compliant VAPT process that meets global security benchmarks like ISO 27001, NIST, and OWASP.